Owasp Firmware Security Testing Methodology
Particularly PTES Technical Guidelines give hands-on suggestions on testing procedures and recommendation for security testing tools. Open OMTG_DATAST_011_Memoryjava and observe the decryptStringimplementation.

Cheatsheet Owasp Iot Testing Guidance Internetofthings Hacking Security Pentesting Physical Encryption Web Cloud Computer Forensics Web Security Iot
A typography associated with your site may be used to acquire many different conceptual methods just like the surroundings your building supplies shelter exposure its design method cantilevering subterranean how its observed public private as well as the way takes advantage of it has the situation views.
Owasp firmware security testing methodology. The mission of OWASP Software Assurance Maturity Model SAMM is to be the prime maturity model for software assurance that provides an effective and measurable way for all types of organizations to analyze and improve their software security posture. Pleased to release the first Firmware Security Testing Methodology under owasp. Refer to OWASPs Firmware Security Testing Methodology to help with identifying vulnerabilities.
4108 OWASP Testing Guide Most recent version is 40 It integrates with other two OWASP document. The OSSTMM methodology Open Source Security Testing Methodology Manual allows testers to customize their assessment to fit the specific needs or the technological context of your company. Firmware Reviewer provides in-depth firmware analysis binaries file systems containers virtual machines IoT UEFI Appliances Network Devices Smart Meters Surveillance dev.
OWASP Top 10 is not what anyone will ask you in an interview. A blog about quick Information Security tools tricks and information. This course will allow you the Gain the ability to do a Complete Web Application Audit and create that book.
The OWASP ASVS is a phenomenal testing methodology for faster tests where your primary goal is making sure youre not missing something major. Especially from third party software. These facts provide actionable information that can measurably improve operational security.
The Firmware Security Testing Methodology FSTM is composed of nine stages tailored to enable security researchers software developers consultants hobbyists and Information Security professionals with conducting firmware security assessments. Created by the collaborative efforts of cybersecurity professionals and dedicated volunteers the WSTG provides a framework of best practices used by penetration testers and organizations all over the world. MASVS is the WHAT MSTG is the HOW Online videos articles.
firmware security testing methodology FSTM. Infact It is the OWASP Testing Methodology they are looking for. It breaks things down by the risk of the application youre testing based on three levels.
The methodology is composed of nine stages tailored to enable software devs and InfoSec pros with performing firmware security assessments. The Open Source Security Testing Methodology Manual OSSTMM focuses on what to test instead of how to test it and contains web security testing basics as well as information about how to interpret the results of the tests. OWASP Web Security Testing Guide The WSTG is a comprehensive guide to testing the security of web applications and web services.
I want to teach you this methodology and help you differentiate yourself from the rest. OWASP Firmware Security Testing Methodology Firmware Security. Opportunistic meant for all software.
OWASP Firmware Security Testing Methodology Penetration Testing Execution Standard Penetration Testing Execution Standard PTES defines penetration testing as 7 phases. OWASP SAMM supports the complete software lifecycle including development and acquisition and is technology and process agnostic. OSTMM helps us to know and measure that how well security works.
November 6 2019. Information Gathering OWASP Mobile Security Testing Guide 2018 0x05a-Platform-Overviewhtml Information Gathering Example. Open Source Security Testing Methodology Manual OSSTMM is a peer-reviewed manual of security testing and analysis which result in verified facts.
From a technical perspective OSSTMM is divided into four key groups. The full release is available via httpstcoq9CIvKssOr. Refer to OWASPs Web Security Testing Guide and ASVS projects for additional.
For dynamic web testing and binary runtime analysis the quickest way to get started is downloading the latest IoTGoat-x86vmdk VMware and create a custom virtual machine using the IoTGoat disk image.

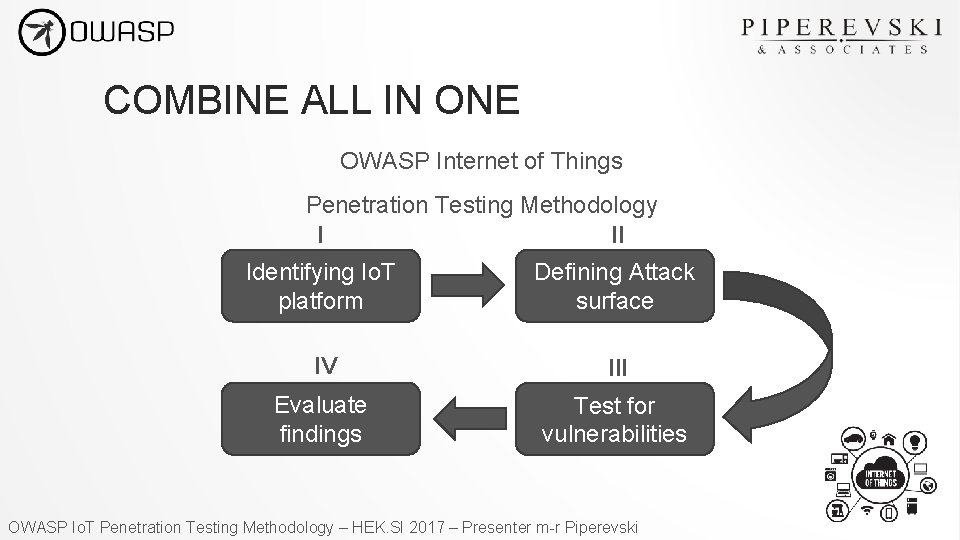
Owasp Internet Of Things Penetration Testing Methodology Owasp

Pdf A Security Assessment Methodology For Critical Infrastructures

Iot Testing Tools Methodologies For Building Resilient Iot Platforms Radiostudio Iot System Testing Innovation Technology

Owasp Firmware Security Testing Methodology
University Of Beds Pen Testing Boot Camp

Our Web Application Penetration Testing Methodology Triaxiom Security
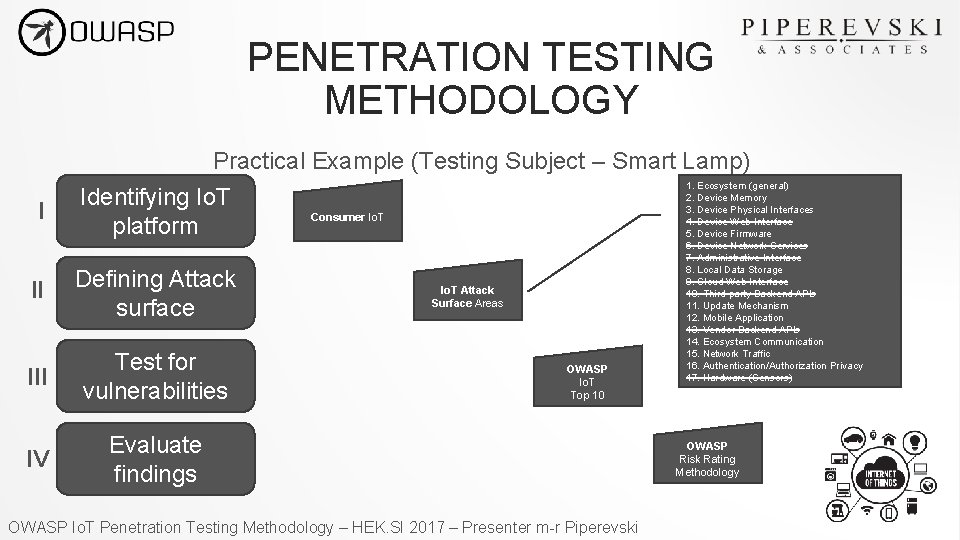
Owasp Internet Of Things Penetration Testing Methodology Owasp
Releases Scriptingxss Owasp Fstm Github

The Steps Performed During The Penetration Test Based On The Flowchart Download Scientific Diagram

Owasp Internet Of Things Penetration Testing Methodology Owasp

Security Reviewer Knowledge Center Security Reviewer
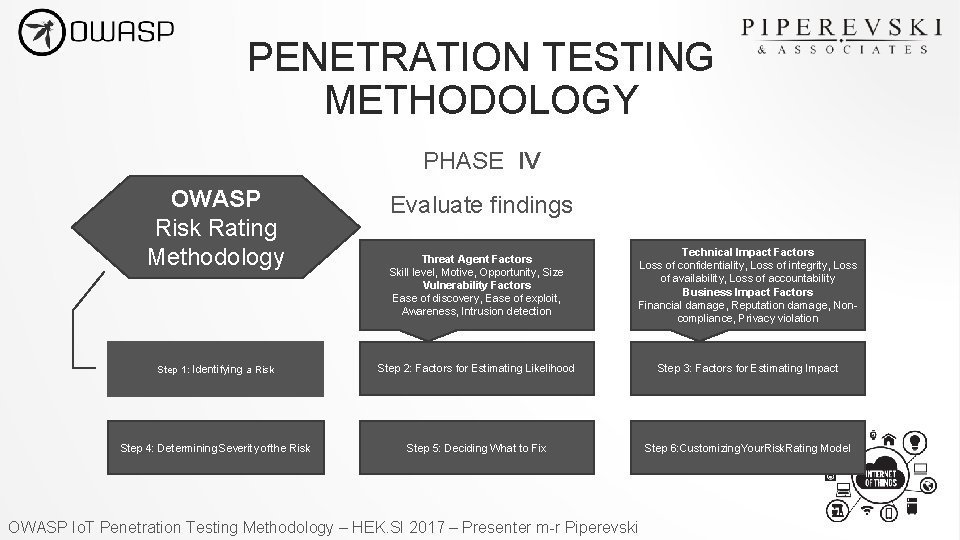
Owasp Internet Of Things Penetration Testing Methodology Owasp
Https Owasp Org Www Project Web Security Testing Guide Assets Archive Owasp Web Application Penetration Checklist V1 1 Pdf
Security Reviewer Knowledge Center Security Reviewer

Penetration Testing Approach Methodology Types Of Tests And Rates

Pdf Standardised Penetration Testing Examining The Usefulness Of Current Penetration Testing Methodologies

Owasp Firmware Security Testing Methodology
Owasp Internet Of Things Penetration Testing Methodology Owasp

Post a Comment for "Owasp Firmware Security Testing Methodology"